Crypto Wallet Audit Services
Wallet Security Audit Services
Apps audited
Vulnerabilities found
Crypto wallets audited
Top-class engineers
Benefits of Crypto Wallet audit by Pharos Production
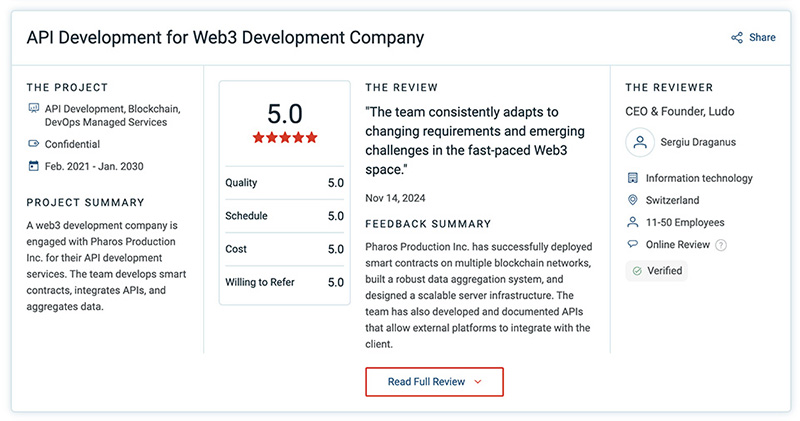
Pharos Production offers industry-leading crypto wallet audit services to ensure the security and reliability of crypto wallets across various blockchain ecosystems. Our expert audit teams specialize in evaluating the security of critical programming languages, including Solidity, Rust, Vyper, Move, C++, FunC, and Tact.
Pharos Production delivers expert wallet audit services, conducting in-depth security assessments to evaluate crypto wallets’ underlying logic, functionality, dependencies, and critical security factors. Our meticulous review process identifies vulnerabilities, ensures compliance with industry standards, and enhances the overall resilience of wallet infrastructures.
Pharos Production provides top-tier wallet audit services, ensuring the highest levels of security for crypto wallets. Our comprehensive audit methodology follows rigorous security protocols and industry best practices to identify and mitigate vulnerabilities in wallet infrastructure, cryptographic mechanisms, and transaction processing.
Pharos Production provides industry-leading wallet audit services, offering in-depth security evaluations to systematically identify, assess, and mitigate vulnerabilities in crypto wallets. Our structured approach follows step-by-step procedures, industry best practices, and advanced security tools to detect potential threats and fortify wallet infrastructures.
An audit can safeguard you against attacks and financial losses
Comprehensive Security Research
Pharos Production delivers industry-leading wallet audit services by adopting a hacker’s mindset to uncover vulnerabilities before they can be exploited. Our approach combines comprehensive functional testing, meticulous manual code reviews, and advanced static and dynamic analysis to assess the security of crypto wallets.
In-Depth Methodology
Pharos Production offers expert crypto wallet audit services to ensure your wallet meets the highest security and functional standards. Our structured approach enhances project integrity by providing comprehensive guidance throughout every phase of the audit.
Dedicated Auditing Team
Pharos Production provides top-tier wallet audit services, ensuring the highest level of security for crypto wallets through a meticulous evaluation process. Our team of skilled engineers and security researchers conducts in-depth audits to assess every aspect of your wallet infrastructure, identify vulnerabilities, and enhance functionality.
Extensive Testing Suite
Pharos Production delivers industry-leading wallet audit services, providing a comprehensive security assessment to identify and mitigate potential vulnerabilities in crypto wallets. Our audit process includes an advanced analysis of attack vectors, utilizing static analysis to inspect code structure, dynamic testing to evaluate live applications, and fuzz testing to uncover hidden security flaws through randomized inputs.
Pharos Production crypto wallet audit
Cryptography and Keys Audit
- Cryptography libraries usage
- Threshold signature review
- Keys generation & storage
- Quantum resistance analysis
- Asymmetric signing and verification
Accounts Audit
- Accounts implementation review
- Wallet implementation review
- Security vector analysis
- Private key recovery
Execution Environment Audit
- Backend implementation review
- Known Server-side vulnerabilities review
- DevOps infrastructure security analysis
- Cloud infrastructure security analysis
Storage Audit
- Storage implementation review
- Data encryption at rest
- Redundancy and data recovery
- Security aspects analysis (DoS, corruption, state implosion)
Chain Audit
- Transaction implementation
- Data structures and integrity
- Bootstrap review
- Mempool review
RPC Audit
- Implementation review
- API endpoint security
- Authentication and authorization methods
- Rate limiting and throttling mechanisms
Let’s ensure your project meets global software development and security standards.
Cybersecurity Act (Regulation (EU) 2019/881)
-
What: Establishes an EU-wide cybersecurity certification framework.
-
Applies to: Software and services that want to demonstrate security compliance.
-
Key points: Certification levels: basic, substantial, high.
NIS2 Directive (Directive (EU) 2022/2555)
- What: Enhances cybersecurity across sectors deemed critical (e.g. healthcare, finance).
- Applies to: Software used in critical infrastructure and essential services.
- Key points: Risk management, incident reporting, business continuity.
Accessibility Standards (EN 301 549)
-
What: Defines requirements for accessible software and websites.
-
Applies to: Public sector digital services and some private sector offerings.
-
Key points: WCAG 2.1 alignment, assistive technology support.
ISO/IEC 27001 (Information Security Management System – ISMS)
-
What: International standard for managing information security risks.
-
Applies to: Any organization aiming to implement an information security management system.
-
Key points: Risk assessment, access control, incident response, continuous improvement, documentation.
HIPAA (Health Insurance Portability and Accountability Act – US law)
-
What: U.S. law protecting medical data privacy and security.
-
Applies to: Software handling Protected Health Information (PHI) for U.S.-based healthcare entities.
-
Key points: Data encryption, audit logging, access controls, breach notifications, business associate agreements.
GDPR
-
What: Regulates how software handles personal data.
-
Applies to: Any software processing personal data of EU citizens.
-
Key points: Data protection by design/default, consent management, user rights (access, erasure, etc.).
Digital Services Act (DSA) and Digital Markets Act (DMA)
- What: Regulates online platforms and gatekeepers.
- Applies to: Software used in digital marketplaces, platforms, or large online services.
- Key points: Transparency, accountability, user rights, interoperability.
PCI DSS (Payment Card Industry Data Security Standard)
-
What: Security standard for handling credit and debit card transactions.
-
Applies to: Any software or organization that stores, processes, or transmits cardholder data.
-
Key points: Network segmentation, encryption, regular audits, access controls, vulnerability management.
ISO 14001:2015 (Environmental Management System – EMS)
-
What: Standard for improving environmental performance.
-
Applies to: Organizations seeking to minimize environmental impact.
-
Key points: Sustainability, resource efficiency, waste reduction, legal compliance, lifecycle perspective.
DORA (Digital Operational Resilience Act – EU)
-
What: EU regulation for ensuring operational resilience in the financial sector.
-
Applies to: Financial institutions, ICT providers, and software vendors serving them.
-
Key points: Risk management, ICT incident reporting, third-party monitoring, penetration testing, business continuity.
Crypto Wallet Audit Services
We will provide you with the best and most experienced specialists for your project.
Wallet Security Audit Services
Wallet Audit Cost
The cost of your wallet audit is determined by several factors:
Cooperation Model
Project Duration
Team Size
Team Composition
Scope of Work
Level of Specialists
We expertly customize expenses to align with your financial capabilities, ensuring you avoid hidden costs through our streamlined processes.
Discovery Stage
1 day
Assess the audit’s scope, timeline, and costs based on the provided documentation.
01
Thorough Preparation
1-2 days
Thorough preparation ensures your project meets functional requirements and best practices, allowing for early identification of potential issues.
02
In-depth Code Review
3-5 days
A thorough analysis of the smart contract’s logic, functions, and dependencies using both automated tools and manual reviews.
03
Extensive Testing
14-21 days
Includes thorough unit, integration, fuzz, and invariant testing, along with advanced attack simulations to comprehensively evaluate your code’s performance.
04
Clear Reporting
2 days
Pharos Production offers a comprehensive understanding of your project’s security status and provides guidance on necessary improvements.
05
Remediation Verification
5-7 days
Includes thorough unit, integration, fuzz, and invariant testing, along with advanced attack simulations to effectively assess your code’s performance.
06
Pharos Production, a Crypto Wallet Audit Services
What are wallet audit services?
Wallet audit services involve a comprehensive examination of cryptocurrency wallets to identify and rectify security vulnerabilities, ensuring the safety of digital assets. These audits assess the wallet’s code, architecture, and security protocols to protect against potential threats.
Why is a wallet security audit important?
A wallet security audit is crucial because it helps detect and address vulnerabilities that could lead to unauthorized access or loss of funds. Regular audits ensure the wallet’s security measures are up-to-date and robust against evolving cyber threats.
What does the crypto wallet audit process involve?
The crypto wallet audit process typically includes the following:
- Code Review: Analyzing the wallet’s source code for potential vulnerabilities.
- Security Assessment: Evaluating encryption methods, authentication mechanisms, and data storage practices.
- Penetration Testing: Simulating attacks to identify exploitable weaknesses.
- Compliance Check: Ensuring the wallet adheres to relevant security standards and regulations.
- Reporting: Providing a detailed report with findings and recommendations for remediation.
How often should wallet audits be conducted?
Wallet audits should be conducted regularly, especially after significant updates or changes to the wallet’s code or features. Regular audits help maintain a high level of security and trust among users.
Can wallet audits prevent all security breaches?
While wallet audits significantly reduce the risk of security breaches by identifying and addressing vulnerabilities, they cannot guarantee complete immunity. Continuous monitoring and adherence to best security practices are also essential to maintain wallet security.
What are common vulnerabilities found during wallet security audits?
Common vulnerabilities include weak encryption methods, inadequate authentication processes, insecure data storage, and flaws in transaction handling. Identifying these issues during an audit allows for timely remediation to enhance security.
How does Pharos Production approach wallet audit services?
Pharos Production employs a structured approach to wallet audits, encompassing code review, security assessments, penetration testing, and compliance checks. Our team of experts ensures that cryptocurrency wallets are secure, reliable, and compliant with industry standards.
What types of wallets can be audited?
Both hot wallets (online) and cold wallets (offline) can be audited. This includes mobile wallets, desktop wallets, hardware wallets, and web-based wallets. Each type requires a tailored audit approach to address its unique security considerations.
How long does a crypto wallet audit take?
The duration of a crypto wallet audit varies based on the wallet’s complexity and size. Generally, it can take from a few days to several weeks. Pharos Production works closely with clients to establish a timeline that minimizes disruption and ensures a thorough assessment.
How can I engage Pharos Production for wallet audit services?
To start a wallet audit with Pharos Production, please reach out to us via the contact page on our website or email us directly. We will arrange a consultation to discuss your needs and outline a tailored audit process that fits your requirements.
FAQ
We have gathered all the common questions our clients frequently ask about crypto wallet audit services and wallet security audit.
Let's collaborate on your new project!
We are pleased to inform you that by clicking the Send button, Pharos Production will take responsibility for your personal data following our Privacy Policy, ensuring you receive tailored information that meets your needs!
What happens next?
01
NDA
After processing your request, we will contact you to discuss your project requirements in detail and finalize an NDA to ensure confidentiality.
02
Plan the Goals
After discussing your goals, requirements, and expectations, we will create a project proposal that includes the scope of work, team size, timeline, and cost estimates.
03
Finalize the Details
We will Google Meet with you to review the proposal and finalize the details.
04
Sign the Contract
We will sign the contract and start working on your project right away.